Qubes OS 3.1 has been released
I’m happy to announce that today we’re releasing Qubes OS 3.1!
The major new architectural feature of this release has been the introduction of Qubes Management infrastructure, which is based on popular Salt management software.
In Qubes 3.1 this management stack makes it possible to conveniently control system-wide Qubes configuration using centralized, declarative statements. Declarative is a key word here: it makes creating advanced configurations significantly simpler (the user or administrator needs only to specify what they want to get, rather than how they want to get it).
This has already allowed us to improve our installation wizard (firstboot) so that it now offers the user ability to easily select various options to pre-create some useful configurations, such as e.g. Whonix or USB-hosting VMs.
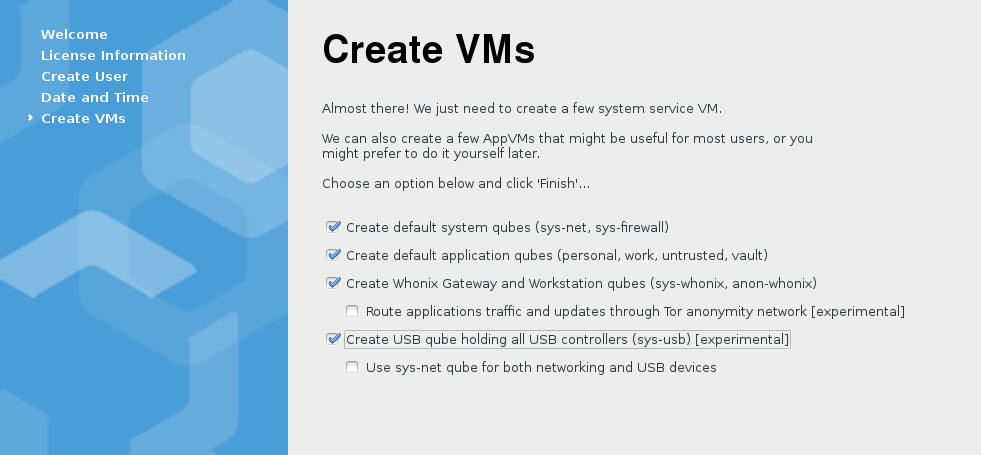
Currently the management stack is limited to Dom0 and system-wide Qubes configuration (i.e. what VMs should be present, with what properties, how connected), and notably missing is the ability to configure/manage states inside the VMs or templates (e.g. what packages to be installed, or what additional services to be enabled in the VMs).
I think most readers should understand very well that marrying a powerful and flexible, yet very complex, management software such as Salt, with a security-focused system like Qubes OS is an extremely sensitive task. This is because we really would not like to negate all the isolation we have previously worked hard to build, obviously.
Yet, we have recently come up with - what we believe is - an elegant way to also extend our management stack to cover the VMs’ internal states. In fact we already have a working code for this and plan on introducing this feature officially in the upcoming Qubes 4.0 release candidate. We might also decide to bring it to the 3.1 release (as an optional update), in case we couldn’t release 4.0-rc1 soon enough.
Once we introduce this missing piece of the Qubes management infrastructure we will gain almost limitless possibilities to shape Qubes configurations to fit particular user groups’ needs and deliver them easily.
Besides the management stack there have been a number of other improvements and bugfixes introduced in 3.1 compared to Qubes 3.0, and most of these have already been mentioned in the original 3.1-rc1 announcement post. To name here just the two which might be of critical importance to some users (as they significantly improve hardware compatibility): Qubes 3.1 now supports UEFI-based boot, as well as many new GPUs, thanks to the updated drivers and kernel in Dom0.
The ISO can be downloaded here. As usual we encourage people to verify integrity of the downloaded images as explained here.
Existing users of the 3.0 and 3.1-rcX releases should be able to easily upgrade without re-installing. Enjoy!